Cyber Strategies
Safeguarding national security, infrastructure, and business arenas in an age of distributed workforce, exploding IOT, and the disappearing concept of "endpoint"
Moving Beyond Zero Trust.. back to basics
It is not the mechanics of cyber security that stump or harm so many organizations or networks. It is, rather, the discipline and methodology of applying these often tedious toolsets and steps. We provide coaching, evaluation, and leadership for government and private sector cyber architectures, distributed environments and workforces, SOC, and emerging cyber technology.
Endpoint Security
Defining, monitoring, and managing full endpoint security across user IOT arenas
Malware Defense & Response
OPSEC and user training to better safeguard from malware hijacks
FedRamp & NIST
Government & vendor cloud protection standards for data and IT security

White Hat for Space Systems
Satelite bus, gyroscope, and other signal disruption, acquisition, and replacement
Space & Satellite Cyber
Satellite, ground station, and infrastructure cyber defense and test design
FISMA Compliance
2023 -24 cyber compliance for government agencies & their vendors

Endpoint? What the heck is an endpoint in 2023?
It used to be simple to monitor a network. But today, with so many fuzzy edges to any network and so many virtual workerforces, with call centers and tech support from anywhere in the world, most cyber teams cannot even define their network, much less identify all of its endpoints. We help US Federal and commercial clients better visualize, define, and manage operational endpoint security across arenas, functions, and geographical locations. It is increasingly common in 2023 to find that the worst ransomware and other cyber breaches have their point of entry with the tiniest of IOT devices used by an undisciplined worker or contractor - such as a Chinese- made camera or NEST device - that then provides entry to the entire network.
This includes toolset identification and integration with existing IT and cyber architectures, training in network and endpoint visualization, and consideration of foreign networks and devices utilized by US and foreign workers and teams, at home and on office premises.
FedRamp Audit-Ready in 2-3 months
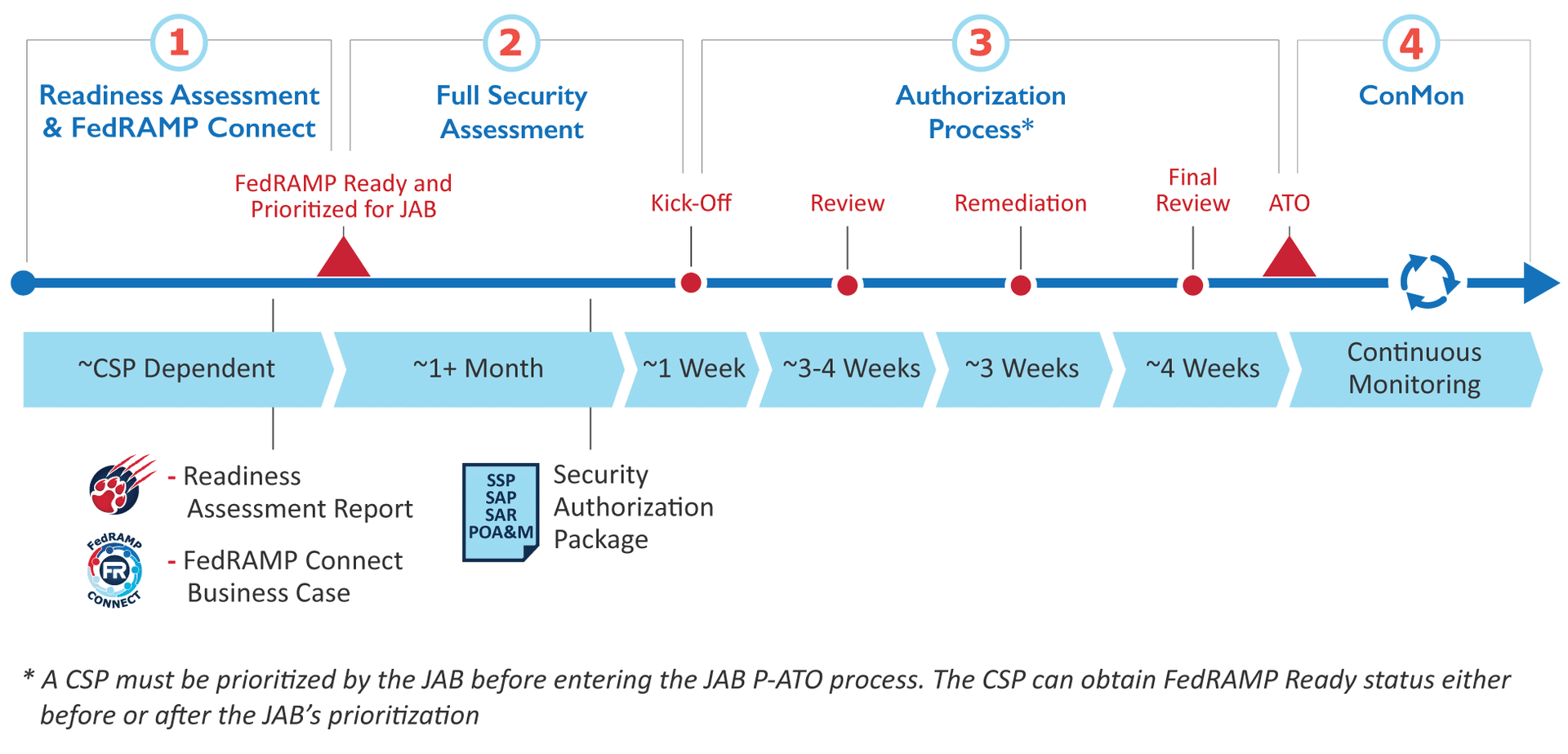

FedRAMP is still the gold standard for US government agency and vendor cyber readiness. When FedRAMP POAMs (readiness milestones, and US military / federal OPSEC (operational security) is achieved, and users - including tech support and third party vendors - are repeatedly trained and tested in both protocols, the network is almost infallible. Most malware, DOS, hash, and other cyber intrusions occur because of sloppy cyber - IT protocol, and/or user error or inattention.
We help clients understand and prepare for FedRAMP compliance testing; and provide refresher training and evaluation services for both this cyber protocol and OPSEC. Once an entity or agency becomes versed in FedRAMP, the problem areas of so much cyber intrusion - failure to synchronize OS or software updates, failure to monitor direct endpoints or access from personal devices, off-network use from on-network devices - disappear. Your surface is hardened, and your workforce and managers are well-trained and the nuances of cyber defense become habit.

FINANCIAL CYBER: A $3 TRILLION MIGRATION
Capital One and the World Bank
Our financial cyber advisory includes the migration of Capital One's $3 trillion in portfolio managment to its new IT HQ in Richmond, VA. And World Bank crisis mitigation advisory following a breach to its Washington DC HQ. As US military and national intelligence advisors, we specialize in emergency and rapid response protocol. Our early clients include the Egyptian Development Bank, and disaster recovery and backup for AT&T and Anthem call centers.
As the US military expands into European theatre action with the Ukraine war, and as Russian and PRC Chinese sanctions are ordered for US and NATO nations, the demarcation between US and allied critical infrastructure is blurred. NATO was the first to recognize and formalize cyber response and protection for blended domains of military and civilian critical infrastructure.
Our work includes SHAPE, SOCOM, EUCOM, UK, and US vulnerability analysis for White House and other leadership; and space, energy, and financial arena intelligence, cyber support, and training. Including agency, vendor, and Big 4 management training, SOC evaluation, and implementation leadership for adjacent arenas and agencies under NIST and US Homeland Security compliance or contracts.
Protecting US & NATO Critical Infrastructure


US-NATO CYBER RISK
How to harden a surface the US Military does not own or control, but is impacted by?
Zero Trust in traditional cyber and IT networks is achieved through KNOWLEDGE, MANAGEMENT, and CONTROL. But in dual-use (military and civilian) sea, ground, air, and space environments, neither US nor NATO militaries usually own these functions. This level of cyber requires 'awareness' and monitoring - and intelligence - without control.
We have supported projects ranging from NORAD underground water reservoir safety, to missile defense and satellite cyber, to identifying enemy or terrorist intrusion or planned intrusion into US Naval installations including the USN Surface Warfare Center (Indian Head, National Harbor, MD-DC), and PRC Chinese cyber penetration into US Department of Energy and other US and NATO secure buildings in Washington and in London.
Reach out to us for teaming, training, sub-contracting, proposal or prototype support in any of these or other cyber areas.

DC STRATEGIC GROUP
US Navy Top 20 Innovator of the Year

DC Strategic Group l DSG Global
